Securing "Work from Anywhere" Access to State and Local Government Digital Applications
In 2022, state and local government agencies remain attractive targets for cyberattacks. Governments are finding that their ‘work from home’ deployments are challenged to meet the cybersecurity requirements since their network perimeter is no longer safely controlled by office locations. Ciena’s Daniele Loffreda and Ralph Santitoro discuss intriguing cloud-centric cybersecurity solutions that help safeguard government networks and IT assets from the everchanging threat landscape.
 Ralph Santitoro is an Edge Cloud Strategist and Architect at Ciena who has defined, architected, and deployed cybersecurity solutions for over a decade. He is also a principal contributor to SD-WAN, SASE, Cybersecurity, and Zero Trust standards in MEF Forum.
Ralph Santitoro is an Edge Cloud Strategist and Architect at Ciena who has defined, architected, and deployed cybersecurity solutions for over a decade. He is also a principal contributor to SD-WAN, SASE, Cybersecurity, and Zero Trust standards in MEF Forum.
State and local government (SLG) agencies continue to be top targets for cyberattack, with nearly 3,236 cyber incidents and 885 data breaches occurring in 20211. This is not surprising, given the breadth of data available contained within agency data bases.
Depending upon the agency, cyber attackers can access or encrypt and deny access to (via ransomware), a wide range of confidential and proprietary information (CPI). These include medical records, payment card numbers, and personally identifying information (PII) such as social security numbers and driver’s license numbers. While most threat actors targeting SLG are considered “general hacking community,” there are a growing number of attacks from “hacktivists” and foreign governments. It was recently discovered that at least six state government computer networks were successfully compromised by a state-owned actor2.
In addition to the volume and variety of data available, other key factors make state and local government agencies attractive cyber targets:
- The adoption of public cloud-based digital government services and applications
- The high value CPI, PII, and access to critical systems that mandate an immediate response to maintain a functioning government
- Employees working from home accessing applications from unmanaged personal devices versus in an office using government IT issued and managed devices
- Internet of Things-connected machine to machine communication (“smart devices”)
The consequences of a state and local government data breach can be significant. Although the $1.93 million average total cost of a public sector breach is lower compared with other industries, additional factors outlined below can dramatically increase the price:
- Agencies managing protected patient information are subject to HIPAA penalties, and those accepting credit cards for payment are subject to Payment Card Industry fines for non-compliance
- Breaches were over $1 million more costly when remote workers were involved, and $1.76 million more where a Zero Trust framework was not deployed3
Threat actors also are confident that their attacks against SLG will remain undetected for a long time. According to a recent data breach report, 47% of public sector data breaches were not discovered until years after the initial attack4. This means that threat actors have an abundance of time to exfiltrate sensitive information about citizens and employees as well as impact critical government infrastructure while avoiding detection. Threat actors have also benefited from the availability of a plethora of hacking tools for ransomware, phishing, and malware deployment.
At the onset of the COVID pandemic, SLG IT teams scrambled to deploy tens of thousands of virtual private networks to enable employees to work from home. Fast forward to 2022 and governments are finding that their work from home deployments are challenged to meet the cybersecurity requirements since their network perimeter is no longer safely controlled by office locations. This vastly expanded security perimeter of a public Internet-accessed, multi-cloud environment facilitates cyber adversaries by increasing the attack vectors available to them to create breaches. As the hybrid work force is more likely to use unmanaged devices and software tools, SLG agencies need to go beyond traditional on-premises threat prevention methods such as physical network-based firewalls, weak password complexity, single factor (username/password) authentication, IP VPNs without access restrictions, and limited visibility of users, devices, and applications that access SLG resources.
Compromised credentials, emails, miscellaneous errors, system intrusion, and basic web application attacks generated most breaches in state and local government5. To address the everchanging threat landscape, a holistic and comprehensive approach to cybersecurity using Zero Trust principles must be taken to provide continuous protection from users running applications on endpoint devices trying to access cloud applications.
One cloud-centric cybersecurity solution that is drawing interest across industry sectors is Secure Access Service Edge (SASE), which combines Software-Defined WAN (SD-WAN) with user, device, and application security functions, which the industry has begun to call Secure Service Edge (SSE)6.

SASE: The merging of networking and cybersecurity
Both SASE and SSE enforce security policies based on user, device, and application identity by contextualizing and continuously monitoring their activity and the risk or reputation of which applications they want to access.
SASE and SSE help safeguard government networks and IT assets by securing access to agency clouds regardless of the user, device, or application requesting access to them. For agency branches, SASE, providing SD-WAN and SSE cybersecurity capabilities is often the optimal solution. SSE will best serve “work from anywhere” employees that connect to SLG publicly and privately accessible clouds over the Internet. Both SASE and SSE typically include the following cybersecurity capabilities seen in the chart below:
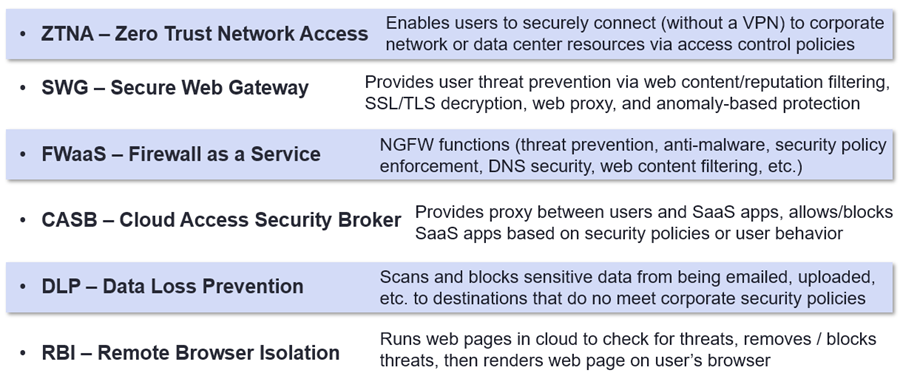
Common SSE Cybersecurity Functions
These combined cloud cybersecurity functions provide one overarching solution that enables continuous verification that helps SLGs mitigate phishing, malware, and ransomware threats. Also, as governments struggle to compete with the private sector to hire and retain qualified cybersecurity staff, the continuous monitoring functions of SASE and SSE is a critical benefit to SLG agencies with limited IT resources. The figure below highlights key SSE components.
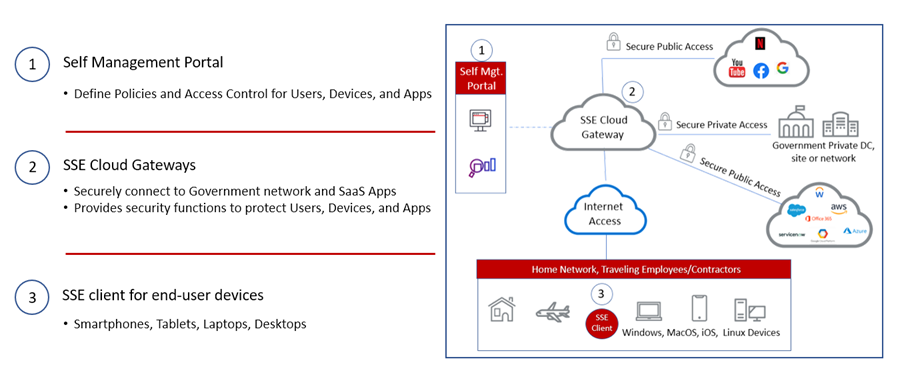
SSE Components
What state and local Governments should look for in a SASE or SSE solution
Each state or local government has a unique set of circumstances to consider when evaluating SASE and SSE vendors, but some general considerations to look at include:
- Secure partitioning of organizations: Select a solution that enables you to isolate government agencies with the ability to apply unique security policies based on the roles of users, devices, and application used within. This isolation is achieved through multi-tenancy (each organization being a tenant), network segmentation (partitioning each network to isolate different organizational domains), and role-based access control (access to the network or networked resources based on the role of the user, device, or application).
- Identity management/authentication system integration: Select a solution that readily integrates into your existing identity management system for secure single sign-on (SSO) using multi-factor authentication (MFA) via popular authentication apps such as Microsoft Authenticator, Okta Verify, and Google Authenticator. All users must be authenticated, authorized, and continuously validated before granted access to private networks, applications, and data. This is the foundation of Zero Trust Network Access, providing privileged access – limiting access only to those who are authorized.
- Protect all types of devices: Many types of devices are used including smartphones, tablets, laptops, desktops, and servers that each run different types of operating systems. Select a SASE or SSE solution that can equally protect each type of device.
- Centralized Policy Management: Select a solution that provides a centralized, common policy management system to protect on-site and remote networked users, devices, and applications to ensure operational efficiency and eliminate the security vulnerabilities that can be introduced when using multiple systems.
Strengthening cybersecurity has been a priority of state government CIOs for the past several years, according to a recent survey of state CIOs7. Implementing a Zero Trust framework with the multiple cloud-based security functions included in a SASE or SSE service, strengthen the cyber security posture at the individual agency level, and across the entire enterprise architecture.
To learn more about how Network Modernization and SASE/SSE can help you achieve a secure “work from anywhere” environment, click here.
1 Verizon 2021 Data Breach Investigations Report
2 CNBC.com
3 2021 Cost of a Data Breach Report, Sponsored by IBM Security, Conducted by the Ponemon Institute
4 Verizon 2019 Data Breach Investigations Report
5 Verizon 2021 Data Breach Investigations Report
6 Reference: Gartner Magic Quadrant for Security Service Edge, 15 February 2022, Authors: John Watts, Craig Lawson, Charlie Winckless, and Aaron McQuaid
7 NASCIO 2021 State CIO Survey
** Third-party trademarks are the property of their respective owners and do not imply a partnership between Ciena and any other company.