How to elevate your defenses against growing cyber security threats in the quantum era
Data and network security continue to be a critical concern for individuals, businesses, and governments, as sensitive information is increasingly being stored and transmitted electronically. And with the average organizational cost of a data breach at $4.35M, ensuring the confidentiality, integrity and availability of data as it traverses the network is essential to mitigate data security risks.
Time-value of information – a new paradigm
Among the many critical data security concerns, advances in quantum computing introduce a new paradigm in data security: time-value of information. The concern is best understood with the concept of “harvest now, decrypt later”, which describes a threat model in cryptography where an attacker steals encrypted data with the intention of decrypting it in the future when a method to quickly decrypt the data becomes available. For organizations with data that retains its value over time, the rapid advances in the computational power of quantum computers make this approach to stealing sensitive data particularly worrisome.
The concept of the time-value of information can be leveraged by a variety of entities, from enterprises to government agencies, to classify the different types of information they deal with. Some information is short-lived in nature, such as financial transactions, and thus its value decreases over time, making it less of a concern for a “harvest now, decrypt later” type of attack. However other types of information, such as Intellectual Property and data with military or national security implications are on the opposite side of the spectrum, with its value maintaining or possibly accruing over time.
Understanding the threat of quantum computers to modern encryption systems
Whereas many symmetric key encryption algorithms, like Advanced Encryption Standard (AES), remain secure at this stage of the quantum era, quantum computers pose a significant threat to many classical key exchange algorithms, which are used to securely establish a shared secret key between two parties for the purpose of encrypting confidential information. One of the key features of quantum computers is their ability to perform factorization and discrete logarithmic computations much faster than classical computers. This makes them capable of breaking today’s widely used key exchange algorithms, such as the RSA and Diffie-Hellman algorithms, which rely on the difficulty of these mathematical problems.
Quantum computers can also use quantum algorithms, such as Shor's algorithm, to solve these problems and compute private keys from public keys, allowing an attacker to intercept and decrypt encrypted communication. As quantum computers become powerful enough to break current cryptographic algorithms, organizations dealing with information that will maintain its value over the next 5-10 years must investigate options available today to mitigate this threat.
What’s next for data security in the quantum era?
Two distinct areas of research and development that have attracted significant efforts and investment over the last several years are Post-Quantum Cryptography (PQC) and Quantum Key Distribution (QKD).
If current key exchange algorithms like Diffie-Hellman are vulnerable, why not create new ones to eliminate that vulnerability? This is the key concept behind the PQC field of activities. The National Institute of Standards and Technology (NIST) initiated an RFC process in 2016 to investigate and develop such new algorithms. The selected algorithms were announced in July 2022 and are currently undergoing the remaining phases of the standardization process. Once these are fully standardized and a certification process is in place to validate their implementation as part of cryptographic systems, the industry will begin introducing them as part of their product offerings. It should be mentioned that the proof of unconditional security does not exist for these algorithms and the assumption is that they will provide resistance against quantum computers unless it is proven otherwise.
QKD systems are a type of quantum communication technology that allows two parties to securely share a secret key. The key can then be used by symmetric encryption algorithms like AES to provide a secure communication channel. In a QKD system, the key distribution mechanism is based on transferring the encoded quantum states between the two parties. Based on the principles of quantum mechanics, any eavesdropping attempt would inadvertently result in the modification of the prepared quantum states and consequently be detected by the communicating parties. Unlike the PQC algorithms described above, QKD systems are considered to provide unconditional security, as the security of the key is not based on the computational complexity of mathematical problems, but rather on the laws of physics.
How Ciena can help elevate your defenses
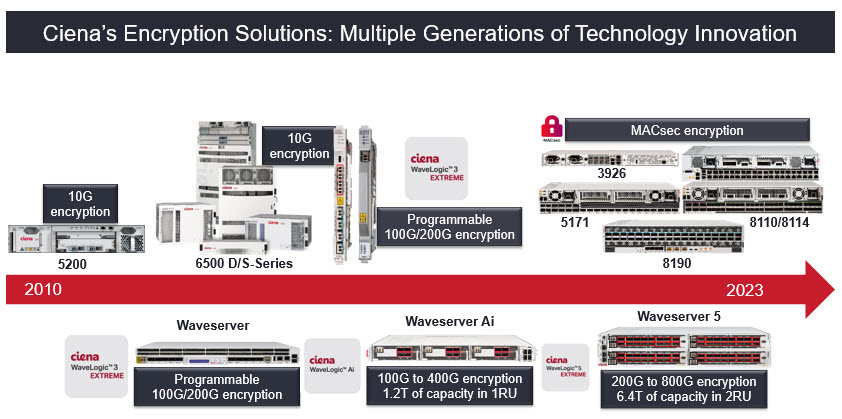
At Ciena, we understand that the journey towards helping our customers elevate their defenses against growing cyber security threats never ends, especially in the quantum era. With this goal in mind, Ciena’s Quantum Communications Design team of experts continues to innovate and is actively collaborating with partners and customers to push the boundaries of what is possible.

Farzam Toudeh-Fallah leads Ciena’s Research and Development Quantum Communications team and brings a wealth of knowledge and experience in the areas of quantum and coherent optical communications expanding over 20 years, going back to his academic and research studies at MIT. His most recent contribution in the field includes collaborating with other scientists from academia and the industry to define the roadmap for quantum communication interconnects, the Roadmap for Quantum Interconnects, published by the U.S. Government.
Ciena’s Waveserver 5 delivered the industry’s first 800G encrypted data rate and uses an innovative optical encryption approach that allows customers to not only deploy a FIPS 140-3 level 2 compliant solution but also provides quantum resistance straight out-of-the-box! How? The implementation combines standards-compliant algorithms and a locally provisioned pre-shared key (PSK) cryptographically, to enable a solution that provides new AES encryption keys every second and adds resistance against Quantum Computer attacks against key exchange algorithms. This allows enterprises and data center operators to deploy an optical encryption solution with programmable wavelength capacities up to 800Gb/s, capable of protecting OTN or Ethernet client signals, including 100GbE and 400GbE, across any distance - from point-point DCI to national and international distances over terrestrial and submarine systems.
What’s next? Interworking of QKD systems with encryption systems is an active field of research and development in the industry, supported by an ETSI standard defining the API for QKD key interface. This interface was leveraged as part of the joint Proof of Concept (PoC) activity performed by Ciena, JPMC and Toshiba that was published last year. Want to learn more? Please join me at OFC 2023 in the Ciena booth to see a demo of Unconditional security of critical data with 800Gbps quantum-secured communications or reach out to your Ciena sales representative.