How to quickly mitigate BGP security risks with route analytics
Customers demand 100 percent uptime and bulletproof network security. In this use case from a large mobile network operator, learn how service providers can mitigate BGP security risks with Blue Planet Route Optimization and Analysis.
In the vast interconnected web of the internet, Border Gateway Protocol (BGP) plays a pivotal role by facilitating the exchange of routing information between autonomous systems (AS). However, the absence of inherent security measures in BGP design exposes it to multiple vulnerabilities. This leaves it susceptible to various attacks, including spoofing, man-in-the-middle attacks, and denial-of-service (DoS) attacks. These exploits can disrupt services, intercept sensitive information, or compromise the integrity of the routing infrastructure. Mitigating these security risks requires proactive measures to secure BGP implementations and detect and mitigate malicious activities.
Let’s explore some of those risks and examine recent events that have led to widespread service outages.
A history of BGP hijacking
BGP hijacking occurs when unauthorized entities manipulate routing information to redirect internet traffic for their benefit. This alarming threat disrupts connectivity, compromises data integrity, and opens the door to unauthorized surveillance. Incidents of BGP hijacking have led to significant disruptions and enabled unauthorized access to sensitive information.
Several notable incidents of BGP hijacking have occurred over recent years. In one case, a national telco intentionally announced false routes in an effort to block YouTube within its borders, diverting global traffic to unintended destinations. Another incident involved ISPs from a particular country hijacking internet traffic, granting unauthorized access to popular websites for their users while causing disruptions for others.
Additionally, one of the largest internet service providers in the world accidentally hijacked substantial portions of internet traffic on multiple occasions, diverting significant amounts of traffic through China.
These incidents serve as reminders of the real-world impact BGP hijacking can have on global internet traffic, network integrity, and user experience. While some incidents were unintentional, others raised concerns about the potential for malicious exploitation of BGP's vulnerabilities.
BGP is also susceptible to accidental configuration changes resulting in widespread service outages.
In another public incident in 2021, several global social media domains went down for a handful of hours after the parent entity accidentally changed its network configuration. This caused it to withdraw its routes from BGP, effectively disconnecting its services from the internet. As a result, DNS resolvers worldwide could no longer resolve the related domains, impacting over 5 billion users. Engineers had to go onsite to data centers to debug the issues and restart systems, which took time due to high-security protocols. The outage also impacted other social media services, as people flocked to alternatives.
In 2022, a major Canadian telecommunications provider experienced a significant outage that had a nationwide impact on voice and data services. The outage occurred due to a planned upgrade to their core network, which unintentionally caused the withdrawal of BGP routes from the internet. This outage had far-reaching consequences, affecting various services such as ATM and debit card payments. As a result, some individuals could not withdraw cash from banks or carry out in-store transactions, while others faced difficulties making emergency 911 calls. Rough estimates indicate that around one-quarter of Canada's internet connectivity was disrupted during this incident.
Route leaks, whether accidental or malicious, lead to the propagation of incorrect routing information across autonomous systems. This can cause unintended traffic flows, congestion, and potential security breaches. Network disruptions and data manipulation are unfortunate consequences of these incidents.
The finance sector is one industry that fights numerous threats, even up to a few thousand, every day. So, what can service providers do when their financial services customers demand 100 percent uptime and bulletproof network security? In particular, what can they do when they’re concerned about risks from BGP route leaks and the potential for malicious attacks?
Let’s look at a use case from a large mobile network operator.
Mitigating BGP security risks for a European mobile operator
One of Europe’s largest mobile network operators owns multiple autonomous systems, each with operating units that cater to different customers. The operator was concerned about BGP security since any site could announce a prefix belonging to another and divert customer traffic to the wrong place.
The security issues concerning BGP are well known and can’t be fixed, so the operator had to consider workarounds. Both route hijacking and unintentional leaks can result in serious consequences such as SLA penalties, damage to reputation, or even loss of business.
The operator did use route filters, but—considering the huge number of IP blocks they had and the updates they dealt with every day—there was a high risk of error and shutting out their own customers. The operator also considered other solutions such as digitally signing route updates, or using only a set of known routes, both of which were eliminated because they were not scalable. Additionally, during a BGP hijack, they could not check their own BGP router’s routing table. This is because, to avoid routing loops, BGP would not add routes set with the local AS in the AS_Path attribute back to that same router.
The network operator required a solution that could alert them in real-time to possible BGP security incidents without adding network overhead. They implemented Blue Planet® Route Optimization and Analysis (ROA). Blue Planet ROA’s BGP baselining capability keeps track of the normal/expected BGP routes for all the BGP border routers and alerts the operator immediately when a route goes missing or a new route appears. Thus, when an AS announces a new prefix, ROA alerts the operator and can verify if the prefix change is genuine or a possible attack.
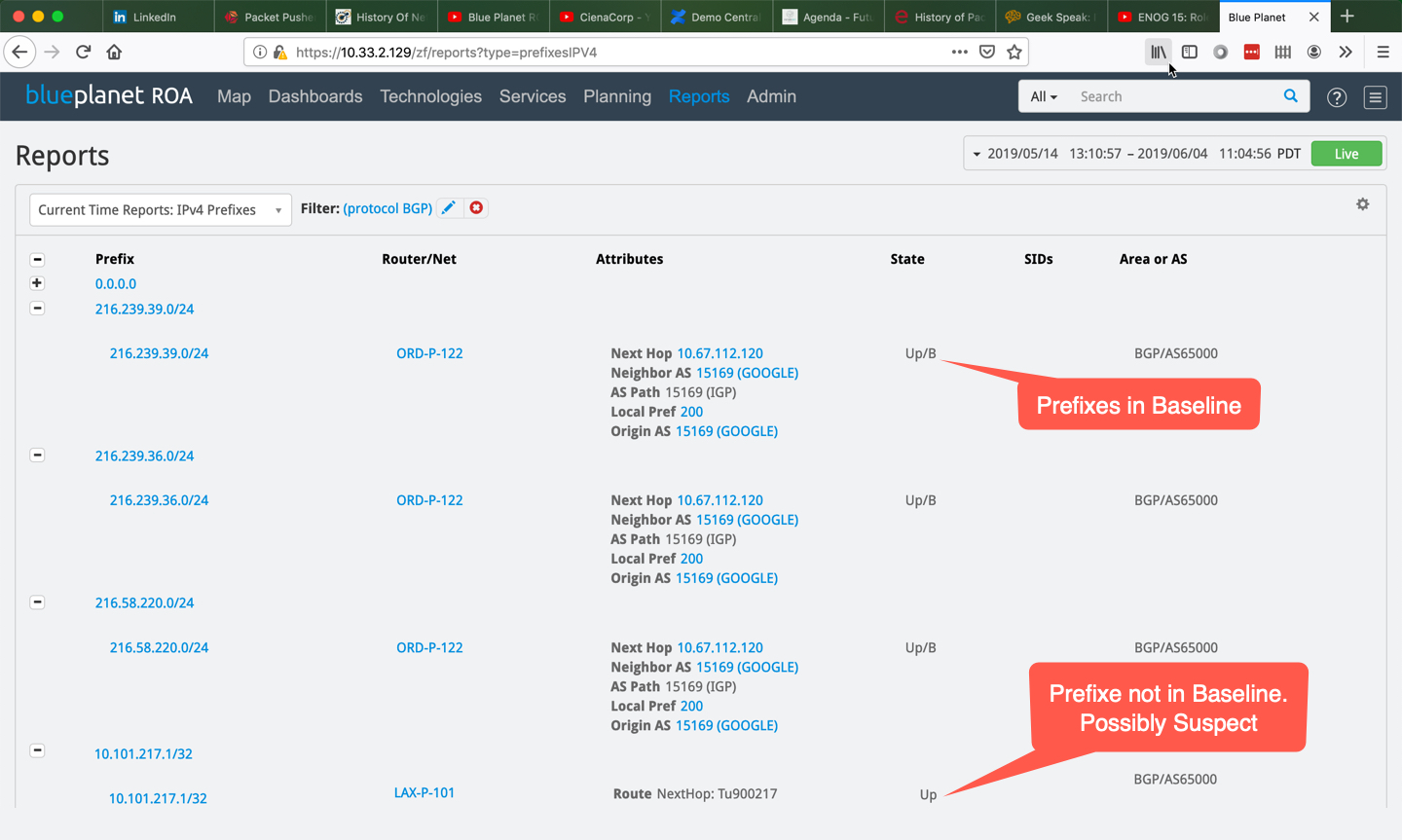
ROA monitors BGP routing and detects prefixes not in baseline.
With ROA in place to monitor interior gateway protocol (IGP) and BGP, the operator can quickly respond to route hijacks, leaks, and various BGP issues, helping solve routing issues even before their customers report an issue. The service provider also uses route analytics to make informed decisions about optimizing their routing and peering.
Blue Planet ROA gives service providers the ability to quickly detect and respond to BGP security incidents, minimizing potential impacts on customers and meeting their demands in today's interconnected world. See firsthand how route analytics can optimize routing and peering decisions, elevating your network's performance and resilience.